Under traditional power communication methods, the security protection technical measures of power industrial control systems can effectively block the intrusion and propagation of conventional viruses from the internet. However, against the dual backdrop of intelligent and interactive development in power systems and the evolution of cyber attack techniques, power industrial control security faces new challenges
The power industrial control vulnerability mining system provided by KeLiang leverages the power system real-time simulation platform RT-LAB, integrated with a power industrial control equipment vulnerability mining module. It enables vulnerability mining for industrial control systems such as SCADA, DCS, and PLC controllers. The system simulates security detection and protection schemes for multiple types of industrial control equipment in power systems. It lays a foundation and provides technical support for security testing in future highly integrated cyber-physical power system attack-defense scenarios, Energy Internet+, and Industry 4.0. Additionally, it offers an effective development, testing, and simulation platform for future research on power system industrial control security
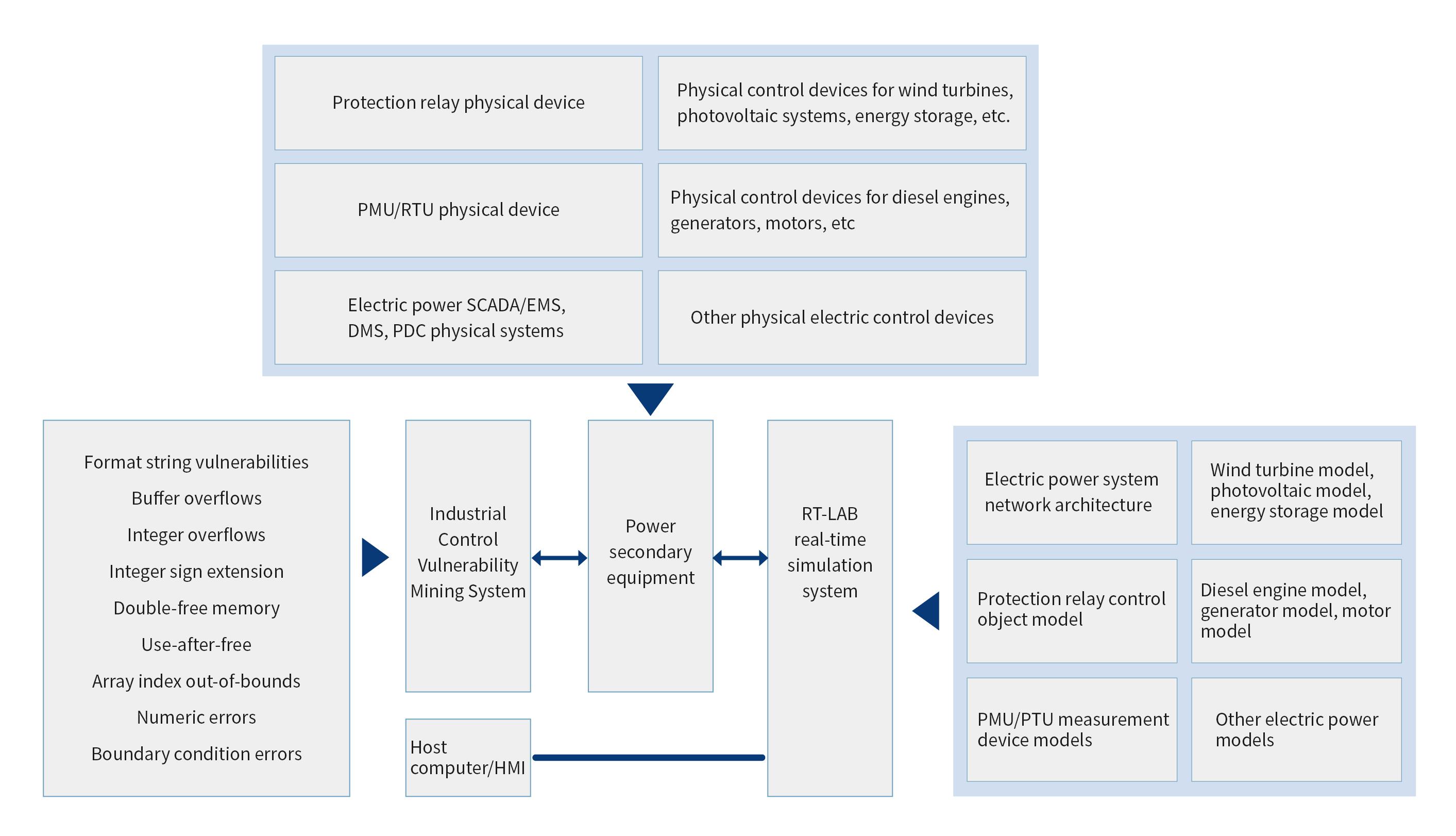
The Power Industrial Control Vulnerability Mining System consists of three components: a power simulation system, an industrial control vulnerability mining system, and the tested secondary power equipment. The secondary power equipment connects to the power simulation system via I/O interfaces and links to the industrial control vulnerability mining system through high-speed interfaces.
Power simulation system: Based on the RT-LAB simulation power system model, it includes the power system grid structure, photovoltaic model, energy storage model, wind turbine model, generator set model, transmission system model, etc;
Industrial Control System Vulnerability Mining System: Targeted at industrial control devices (PLCs, industrial PCs, PMUs, protection relays, etc.) for vulnerability mining. The vulnerability types encompass communication protocol vulnerabilities, embedded system vulnerabilities, control command vulnerabilities, along with format string vulnerabilities, buffer overflows, integer overflows, integer sign extension vulnerabilities, double-free memory errors, boundary condition errors, etc.
■ Power industrial control equipment environment simulation and emulation
■ Vulnerability detection and security defense for power relay protection industrial control devices
■ Vulnerability mining and active defense for critical power equipment control systems (e.g., wind turbine control systems, etc.)
■ Vulnerability detection, alerting, and security defense for power monitoring industrial control devices (e.g., PMUs, RTUs, etc.)
■ Fuzz vulnerability mining and security defense for power monitoring systems (e.g., SCADA, EMS, DMS, PDC, etc.)
■ ntelligent management of vulnerability mining tasks, automated management of industrial control protocol test cases, and online real-time analysis of industrial control protocol data.
■ Research on vulnerability mining algorithms and active defense algorithms for power system industrial control.
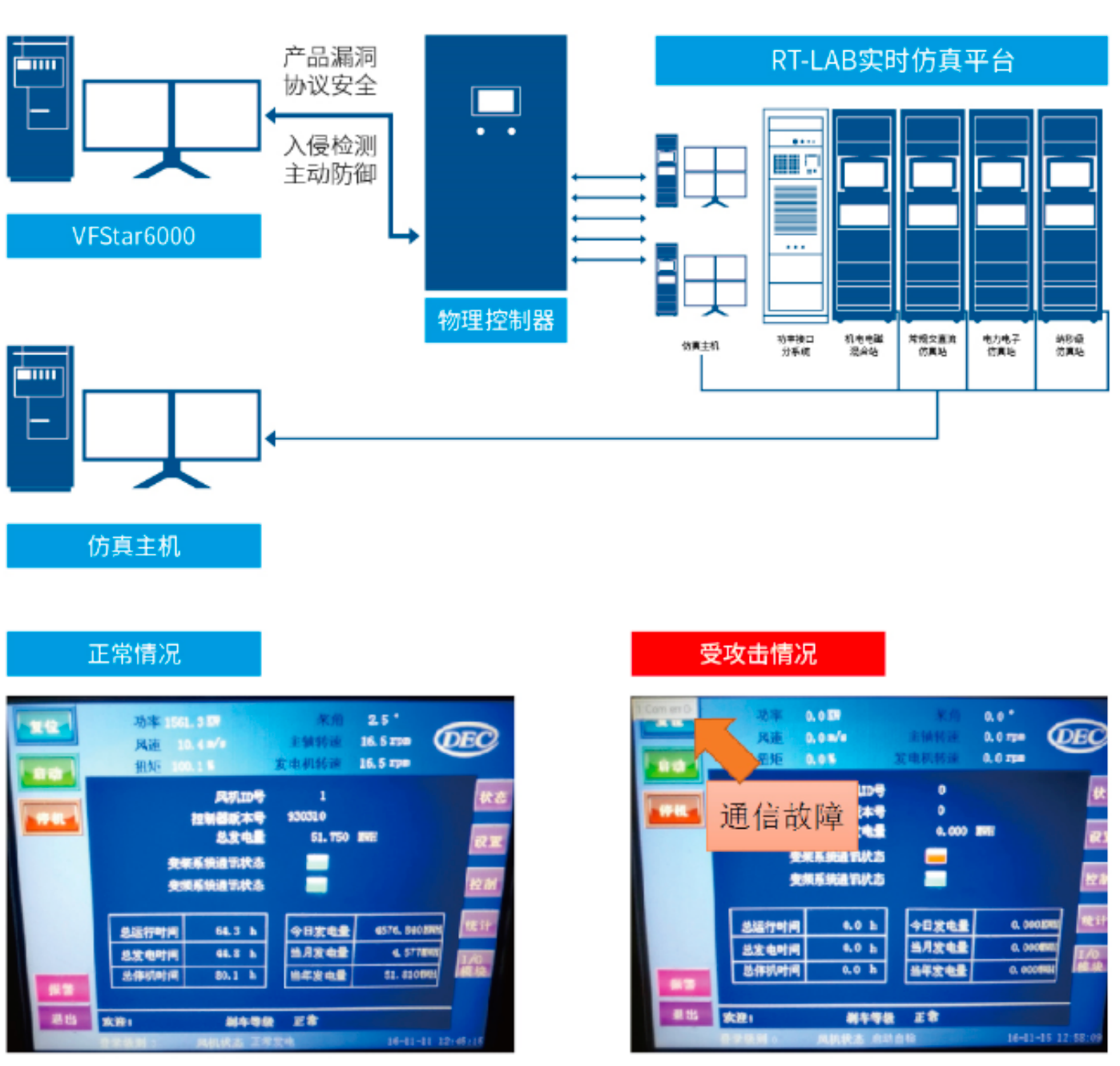
The power industrial control equipment vulnerability mining system provided by KeLiang has successfully established a large-scale wind turbine industrial control information security test platform. Within this platform, RT-LAB simulates the large-scale wind turbine model, while the actual wind power control cabinet is connected to RT-LAB via high-speed I/O interfaces to achieve HIL (Hardware-in-the-Loop) simulation. Simultaneously, it establishes a real-time communication connection with the industrial control vulnerability mining system.
Under this industrial control information security test platform, the vulnerability mining system can uncover various potential security vulnerabilities. It can also simulate scenarios where hackers exploit these vulnerabilities to cause communication failures. Under normal conditions, the wind power control cabinet operates correctly; however, after being attacked, the wind turbine controller displays communication failures, and the wind turbine monitoring system outputs power failure alerts.
This large-scale wind turbine industrial control information security test platform can simulate and analyze security issues of wind power control cabinets. It facilitates vulnerability mining for existing wind power control cabinets, predicts their security status, and provides proactive security defense solutions.